Our Solutions
Be Ready
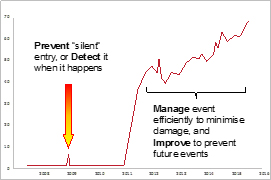
Our solutions cover personnel training for your internal IT professionals, processes & procedures, and software & hardware solutions – to enable the prevention of an attack, to identify it at the initial stage before damage is done, to manage Cyber Attack events to minimize damage if they occur, and to effectively identify and track the source to improve future defense.
Providing security for the Industrial Internet and critical environment requires:
- An Industrial Mindset and engineering track record
- Understanding of Industrial Process integrity and Zero down time
- Cyber Expertise around Operational Technologies
ICARE Cyber Combines all those disciplines in a unique solution.
Our solutions focus on 3 core areas
• Training: People training to be able to prevent an attack, identify it at point of entry, and to be able to manage the emergency if the attack is successful
• Processes & Procedures: Create and implement a set of Standard Operating Procedures for the organisation to prevent from attacks
• Systems & Technology: Data monitoring, control and event management capability to be able to monitor, capture and analyse events in real time as they occur

Our Approach
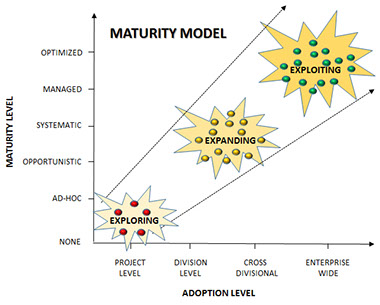
Our approach is to conduct an initial Gap and Risk Assessment to define the level of maturity of our customer around People, Processes & Procedures and Systems & Technology.
Together with the customer, we define an “As Is” and a “To Be” stage and provide a comprehensive solution from implementation through to daily operation.
1. Pre-Study
2. Maturity Assessment
3. GAP Analysis
4. Solution Formulation
5. Agreement
6. Implementation and Know How Transfer
Cyber by Design

Gap & Risk
Analysis
Versatile Environment
Data Bases
Remote Access
Connection between Networks
Auditing
Data Leakage
Prevention
ICS Compliance
Files Sanitations
Segregate Network's
Secure Data Transfer
Secure Remote Connections
Real Time Protection
Monitoring
Detection
Mitigation
Investigate
Reporting
After Action Analyses
IT Infrastructure
OT Infrastructure
Risk Assessment
Risk Monitoring
Investigation Technology
Forensic
Detection of Attacks
OSOC for SCADA Systems
Design & Build SOC
Secure Architecture
Consulting
Implementation Phase
Define the Opponent
Attack Vectors
Management Commitment
Defining Technology Road Map
Advantage
IT Infrastructure
OT Infrastructure
Environment Emulators
Attack Modeling
Investigation Technology
War Games
Secured
Architecture
Model
Cyber Security
Policy
Security Operation
Centre
Cyber
Training
SCADA
Defense
Response
Team

Contact
For further details, please don’t hesitate to contact us:
+41 22 960 7602
info@icare-cybersecurity.com
© 2016 ICARE - Rue Faucigny 5, CH – 1700 Fribourg - Switzerland